EN: Gynvael’s Mission 016
My task⌗
I wasn’t in a hurry to accomplish mission no. 016 (in decimal), because I’m an author of this mess ;) So in this post I will show “my intended solution”. Before we begin, I want to give a huge shoutout to my IRC mate, who have told me a lot about a SSTV and a ham radio. This inspired me to create this mission. Kudos to @fishcake! The rating of this mission was done by @Gynvael.
So what were the orders?
MISSION 016 goo.gl/zqvPQD DIFFICULTY: ████████░░ [8╱10]
┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅┅
Operation codename: "Pasokon"
During the operational game our spy (codename "Martin") managed to intercept
hostile communication.
goo.gl/MoYBAx
Unfortunately, we have no idea how to decode it. To make matters worse, our most
well versed in crypto agent (codename "Scottie") is on a mission right now and
cannot help us. Your handler advised to use your skills.
The fate of the Chunar rests in your hands!
And remember - if something is not clear, you have a license to bruteforce.
Good luck!
Over and out.
--
If you find the answer, put it in the comments under this video! If you write a
blogpost / post your solution / code online, please add a link as well!
P.S. I'll show/explain the solution in a video in one or two weeks.
P.S.2. This mission was brought to you by foxtrot_charlie!
Oh hack… All specialists are deployed, so once again we have to save the world ;) today’s world is called “Chunar”…
Intel⌗
Let’s start simply by downloading a file that is located under a link shown in a mission description.
What is it?
Huh, a txt file with some weird encoding. If you scroll down, there is a = sign.
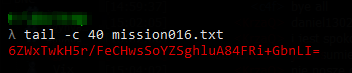
Adding a charset the straight conclusion hits my mind. This is base64! Let’s decode it with commandline tool.cat mission_file.txt | base64 -d > somefile
This command will create binary file. By file, a radare2 \m or simply a hexeditor we can identify this bytes as a wav file. So it’s a sound! Let’s play it!mv somefile somefile.wav
This is not the music unfortunately. Let’s use audacity and search for some patterns in this file.
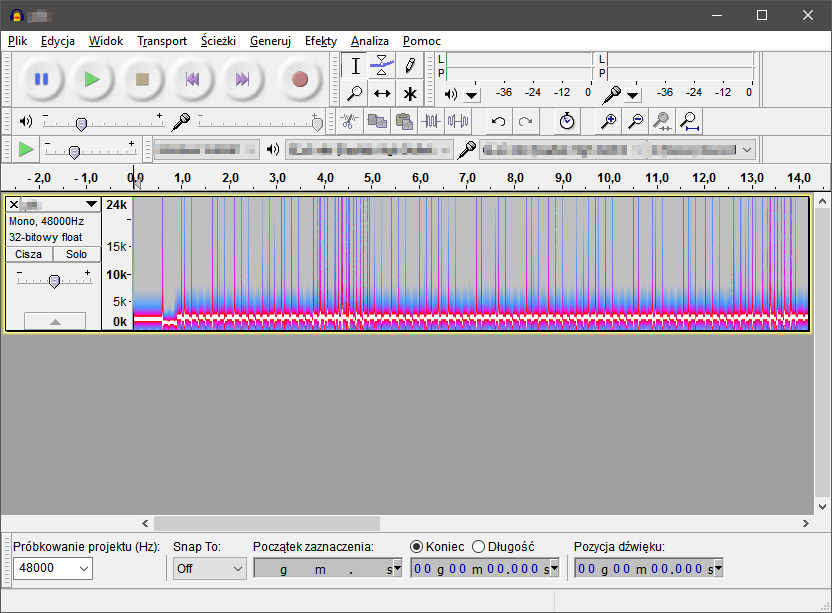
Definitely there is a encoded message. But how to get it? This link should help. Searching by waterfall image shows that this characteristic pattern belongs to the SSTV (Slow-Scan Television). You can even play a sample file to be 100% sure with the identification.
Honestly this was the hardest part of this task. Looking at weird codenames in the description also hints that the SSTV was used to encode image.
Solve!⌗
I used software called RX-SSTV to obtain the image. It looks like this:
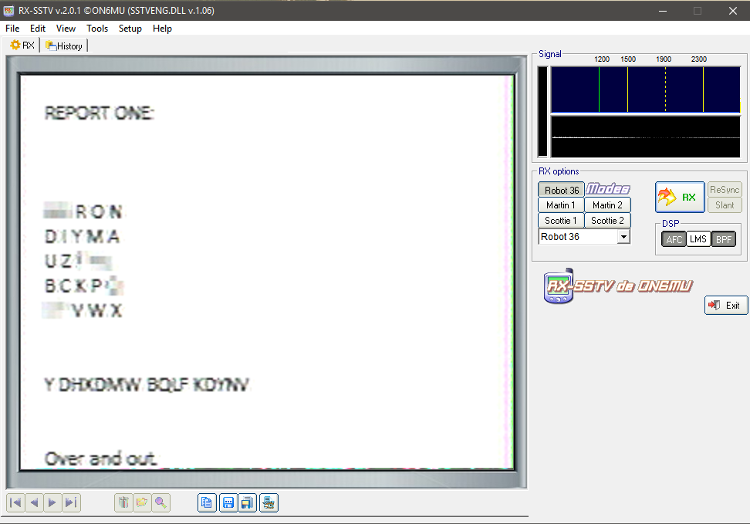
To get the best quality I suggest to either redirect sound from output to input in your soundcard settings or simply put microphone inside close shells of headphones. This is how I got mine. The type of encoding should be automatically discovered by the software. It was robot36 that was not mentioned in the description ;) Now message looks like:
REPORT ONE:
? ? R O N
D I Y M A
U Z ? ? ?
B C K P ?
? ? V W X
Y DHXDMW BQLF KDYNV
Over and out.
So this is not the end of this challenge. Remember what the description told us, if something is not clear it is good to bruteforce it just in case. First and the most important thing is to identify used cipher. What we see is a 5x5 letters matrix. Some of them are blurred. There aren’t many ciphers that use this kind of matrix. The most popular one is a Playfair. Searching for it in Wiki gives us the name of Lyon Playfair. Check where he was born ;) - if you weren’t convinced then now you should. So this cipher is the Playfair. Unfortunately the radio transmissions are vulnerable to some interference and we have to somehow recover damaged matrix to decode it. I really like the way of Pawel’s Lukasik thinking. So if you are interested in cryptanalytic way of finding out the flag check out his blogpost! In such cases I prefer to use the power of CPU and simply try all combinations. I use my Playfair library and this dirty Python script:
import random
import playfair
import itertools
def main():
ph = playfair.Playfair()
left = ["E", "F", "G", "H", "L", "Q", "S", "T"]
part1 = "RONDIYMAUZ"
part2= "BCKP"
part3 = "VWX"
for i in list(itertools.permutations(left, 8)):
pswd = ''.join(i[:2]) + part1 + ''.join(i[2:5]) + part2 + ''.join(i[5:]) + part3
ph.setPassword(pswd)
dc = ph.decrypt('Y DHXDMW BQLF KDYNV')
dc = dc[0] + ' ' + dc[1:7] + ' ' + dc[7:11] + ' ' + dc[11:]
print("Password: {}\tmessage {}".format(pswd, dc))
if __name__ == "__main__":
main()
to decrypt password. The output of this program can be redirected to a file and then using some command like this fgrep -f "first-file" "second-file" with dictionary like rockyou.txt or simply trying to find the line that matches English words the most, the most English flag will be found.
The flag is I ALWAYS PLAY FAIRX. This X comes from the fact that the Playfair cipher needs even number of letters.
That’s all. I hope you’ve enjoyed the mission. I had a lot of fun creating it! From this place I want to give kudos to Adrian Laskowski. He didn’t solve the mission (although he was really close), but he have decoded SSTV bare hand! Gratz, I’m impressed! And kudos to all of you, who solved the mission ;) Thank you for your writeups!
If you are interested what was the password, well I was trying to randomize Playfair’s board a little bit ;) This is how I’ve encoded the message using this website:
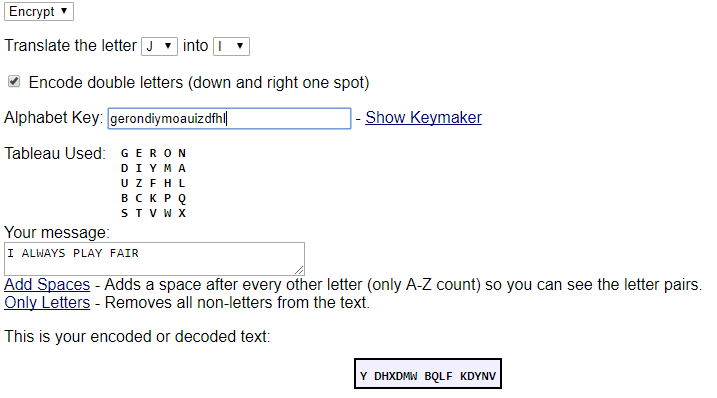
And this is how the image looked before blurring some stuff:

foxtrot_charlie over and out!